
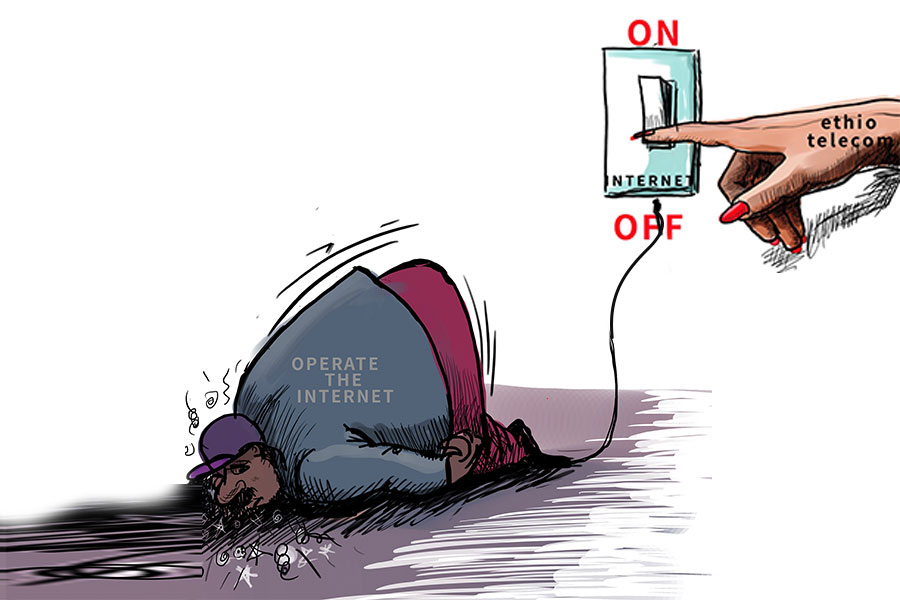
View From Arada | Nov 21,2020
Standing in front of my house, I mused at the utility technicians with their pickups and ladders, going up and down poles, busy connecting households.
“Is everything being connected and that connection maintained every single moment now?” I said to myself.
Just a little while ago, I shared a piece from my life, as a writer aspirant, to a group of book lovers on my Facebook page.
A little while later, I received a friend suggestion from the social media platform of someone I have not seen in more three decades. I did not search for the person, and neither was a friend request sent to me. Facebook “guessed” I might know that person.
It sent a chill up my spine just considering the privacy implications of this. The platform has gathered enough information about the people in my circle to correctly predict my interests and even history.
Is this a fair price to pay to be connected? What does social media – or just communications technology as a whole – offer in return for such private pieces of our information?
It does, in fact, have a great deal to offer. To know what, all one has to do is remember life in a time before the internet, or even when telephones were not that widespread in Addis Abeba.
It is with nostalgia that I remember the first day a landline telephone pole was erected in my neighbourhood when I was but an infant. It was embraced and endearingly kissed by elated grownups.
For decades, that technology remained rickety. Take my time working in fieldwork, a couple of decades back. We would pick up a phone, wait for the operator to answer, or would roll the lever to ring a bell, and then tell the operator who we wanted to be connected with. Every phone call that was made had to be put through by hand. There was no automatic switch for calls coming in from out-of-town areas.
A computer was a gadget that was even more out of reach. My first seven years of public service never allowed me to have a closer look at a computer. The next year did, and I immediately moved to the private sector. Being hooked to the net from my office desk, I cannot forget the rush of excitement as the computer opened.
We were embarking on a new brave world, and many of us were thrilled by it but not necessarily satisfied. There were a couple of guys I met in pub 16 years back. One was a senior citizen to whom a computer meant his whole life and a younger one in his late twenties. I related my astonishment at the ongoing IT revolution. They could not believe this that I really thought it was a “revolution” considering the quality of service in Ethiopia.
As a response to my bewildered look, the older man started to tell us about his wrenching days as a four-digit salaried computer engineer, which afforded him life in a posh apartment, with a high life in the area known as Mosvold in Piassa.
Then, he continued lamenting about how poor infrastructure in Ethiopia distanced him from his beloved field. Then the youngster started to complain of the sluggish dial-up connections of the day and listed the absence of alternative services. Yet, for all his objections, he said life without the fruits of the information age is unthinkable.
It is not always that I agree with such sentiments. Indeed, it takes me a long time to catch up, as my long-lasting iPhone 4, a version of the iPhone lineup released a decade ago, testifies. To test how updated I am with prevailing mobile devices, as well as ceremoniously retiring my iPhone 4, which served me for a decade, I headed to an IT professional, who has a shop very close to my house.
As he started listing the options out there in the market, the virtue he repeatedly underlined about quality revolved around the devices’ security features. As the list was long and he was busy, I told him I would return some other day and headed home as I was obsessed with his concern.
The urgency for security is indeed an urgent concern that should get the appropriate intervention. These are the machines that allow us to essentially deport a digitised version of ourselves into extremely interconnected computing systems. We are unloading a great deal of our information that is later used to draw all sorts of conclusions as well as help us make choices, including how we pay our bills, elect our presidents or even find our life partners.
We are sharing with the assumption of confidence. It should not be betrayed lest the communications technology, which has come this far, loses its edge.
PUBLISHED ON
Nov 14,2020 [ VOL
21 , NO
1072]


View From Arada | Nov 21,2020

Fortune News | Aug 21,2021

Fortune News | Mar 16,2019

Radar | Oct 28,2023
Editorial | Feb 25,2023

Agenda | Apr 19,2025

View From Arada | Dec 28,2019

Life Matters | Sep 07,2019

Commentaries | Apr 30,2021

Viewpoints | May 11,2019

Dec 22 , 2024 . By TIZITA SHEWAFERAW
Charged with transforming colossal state-owned enterprises into modern and competitiv...

Aug 18 , 2024 . By AKSAH ITALO
Although predictable Yonas Zerihun's job in the ride-hailing service is not immune to...

Jul 28 , 2024 . By TIZITA SHEWAFERAW
Unhabitual, perhaps too many, Samuel Gebreyohannes, 38, used to occasionally enjoy a couple of beers at breakfast. However, he recently swit...

Jul 13 , 2024 . By AKSAH ITALO
Investors who rely on tractors, trucks, and field vehicles for commuting, transporting commodities, and f...
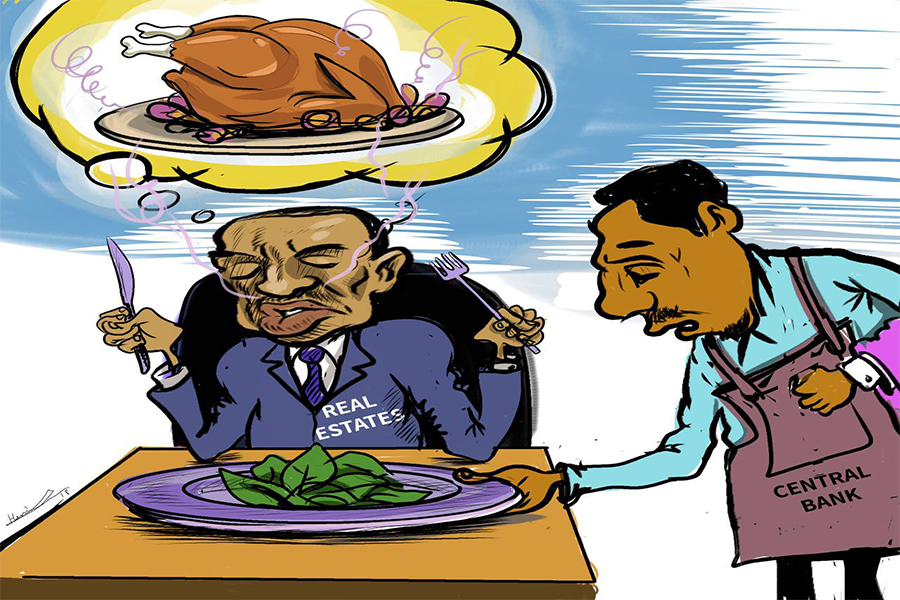
Oct 4 , 2025
Eyob Tekalegn (PhD) had been in the Governor's chair for only weeks when, on Septembe...
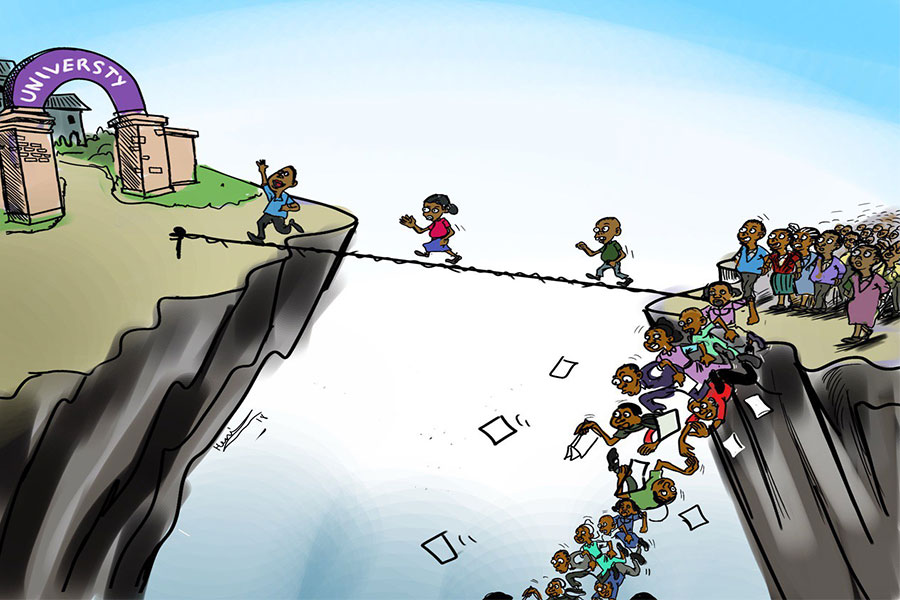
Sep 27 , 2025
Four years into an experiment with “shock therapy” in education, the national moo...
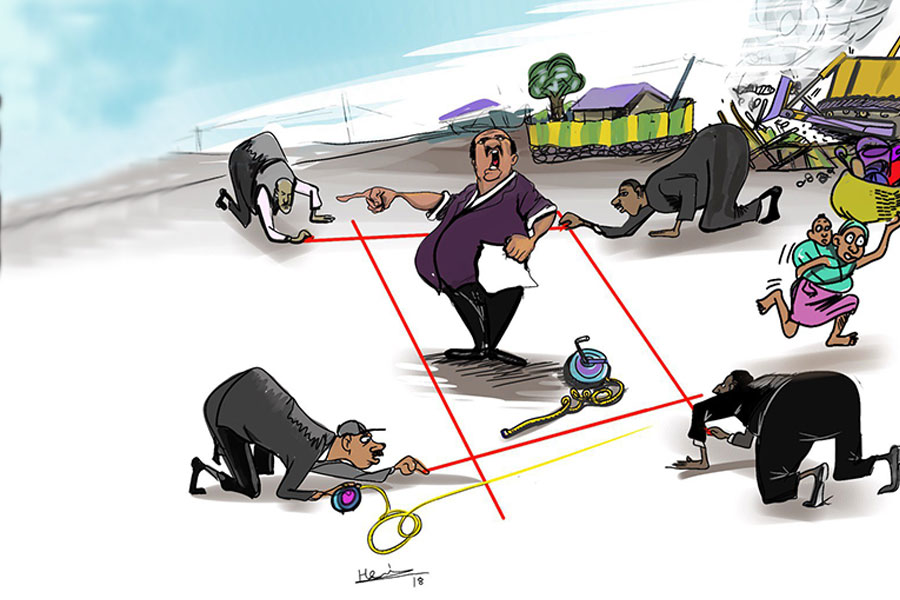
Sep 20 , 2025
Getachew Reda's return to the national stage was always going to stir attention. Once...
Sep 13 , 2025
At its launch in Nairobi two years ago, the Africa Climate Summit was billed as the f...